- Using a library
- Manual verification
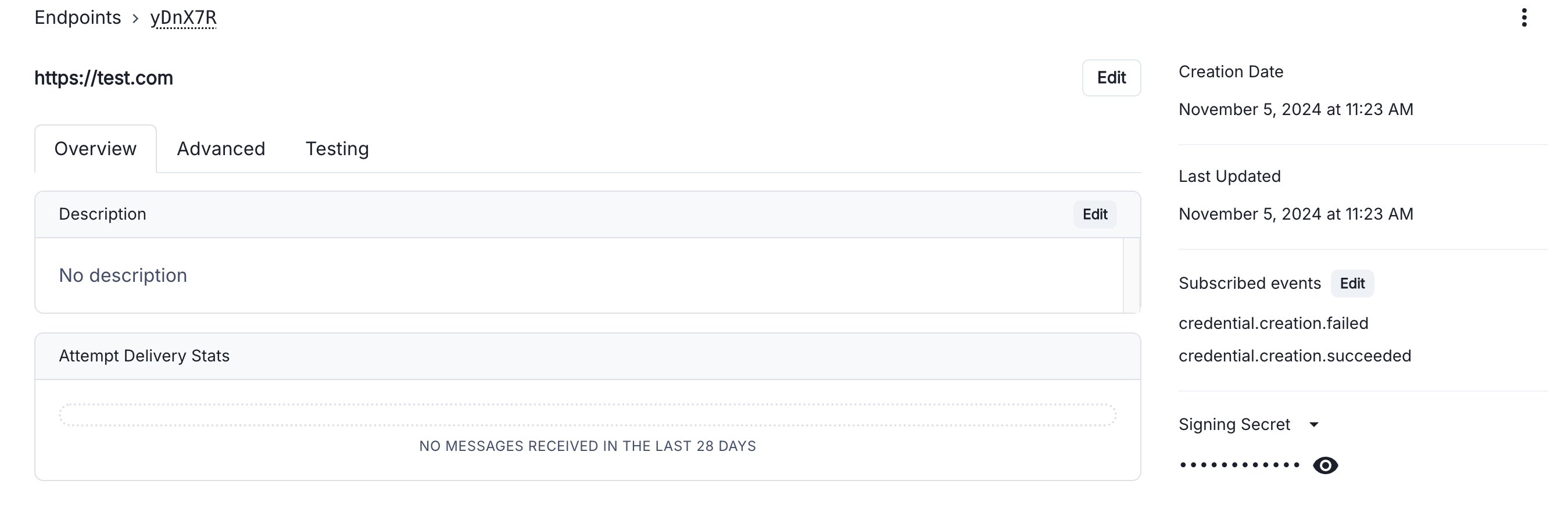
We are going to use the Svix open-source library to verify webhooks. First, install the relevant libraries for your language:Next, verify webhooks using the code below. The payload is the raw (string) body of the request, and the headers are the headers passed in the request.Remember to get the signature secret from the endpoint details in the console.